With the industry talking about Software Defined Networking (SDN) at full hype levels, there is one thing missing from many discussions: the application. SDN promises to reign in the complexity of network infrastructure and provide better tools for deploying services at scale. What often seems to be forgotten are the applications, which are the reason those networks exist. While application focus in itself is not a new concept it seems lost in the noise around SDN as a whole, with a few exceptions such as Plexxi being which focuses on Application Affinity.
Current SDN approaches provide tools to solve issues in one portion or the other of network infrastructure. Flow control mechanisms look to centralize the distribution and configuration of routing and forwarding. Overlays look to build virtual networks on existing IP infrastructure. Virtualized L4-7 services provide solutions to configure, stitch-in and control network services more closely to virtual machines themselves. None of these current approaches looks to tackle the whole picture from an application centric point of view. These solutions also take a myopic view that the VM is the network, this is far from the case. The closest models fall into dev-ops categories or orchestration but these require a deep understanding of the details and intricacies of the network.
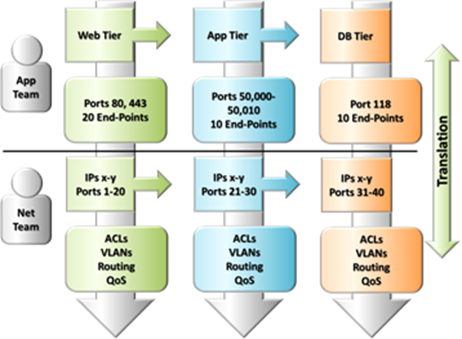
In traditional networking environments there is a disconnect in communication between application and network teams. The languages and concepts are disparate enough that they don’t translate, there is no logical continuation from application developer or owner to network designer. Application teams speak in OS instances, application tiers and components, tooling, language, end-user demands, etc. while network teams speak in switch-ports, VLANs, QoS, IP addressing and Access Control Lists (ACLs). The lack of common understanding and vocabulary causes architectures and implementations to suffer. The graphic below illustrates this relationship:
Building the flexible, scalable, manageable and programmable networks of the future requires a change in focus. The application needs to take center stage; it’s the apps that solve business problems. From this focus, logical and physical topology become secondary and are only designed once application requirements have been mapped out. Application centric policies must be designed first. Policies such as: security, load-balancing, QoS can all be designed based on application requirements, rather than network restrictions. Application developers define these requirements without the need to speak a network language.
Traditional networks begin with a physical topology that is layered with L2 and L3 logical topologies and assumed application mobility and service domains such as a services tier in the aggregation level. Once these topologies are architected and implemented applications are built and deployed on them. This method limits the capabilities available to the application and the services deployed on them.
Application security is an excellent example of a system that suffers from traditional architectures. Network security constructs are implemented in the form of ACLs on switches, routers and firewalls. These entries suffer from two major drawbacks: complexity of design/implementation and scale of the TCAM that stores the entries. This means that application policies must be communicated effectively to network engineers who must translate those requirements into implementable ACLs across multiple devices in the network. This is then defined manually device-by-device. This is a system ripe for PEBKAC errors (Problem Exists Between Keyboard and Chair.)
The complexity and room for error in this system increases exponentially as networks scale, applications move and new services are needed. Additionally this leads to bad practice based on design limitations. Far too often outdated policy entries are left in place due to the complexity and risk of removing entries. This leads to residual entries in place consuming space long after an application is gone. Just as often policies are written more loosely than would be optimal in order to reduce required entries, and optimize space, through wild card summarization.
To break this cycle networking systems need to take an application centric approach which models actual application requirements onto the network in a top down fashion. Systems need to take into account the structure of the application, its components, and how those components interact then provide tools for designing logical policy maps of these relationships. From there these policy maps can be programmatically applied to the networking infrastructure.
An application is not a single software instance running on a server. Applications are made up of the end-points required in a given tier, the tiers required for the service delivered and the policies that define how those tiers communicate, and their unique requirements. The application as a whole must be taken into account in order to provide robust, scalable service delivery.
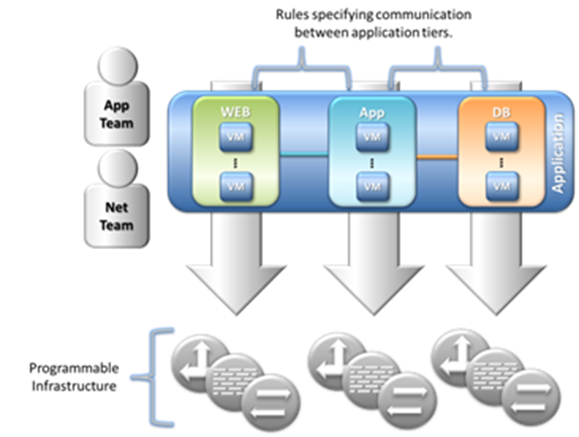
The illustration below shows this relationship in contrast to the diagram above:
In this model network and application teams develop the systems of policies that define application behavior and push them to the network. Taking the application as a whole into focus instead of the myopic view of VMs, switch ports or IP addresses allows cohesive deployment and manageability at scale. The application is the purpose of having a network; therefore the application should define the network.
This definition of the network by the application should be done in a language that the developers understand, and the network can interpret and implement. For example an app owner labels application traffic as ‘video’ and the network implements policies for bandwidth, QoS, etc. that video requires. These policies are predefined by the network engineers.
An application is more than an IP address and a set of rules; it is an ecosystem of interconnected devices and the policies that define their relationship. Traditional networking techniques anchor application deployment by defining applications in networking terms. In order to accelerate the application deployment (and re-deployment throughout its lifecycle) networks need to provide an application centric view and deployment model.
I do not even know the way I finished up ight here, however I thought this post was once great.
I doo not recognise who you’re however certainly you are going to a famous blogger
for those who are not already. Cheers!
Quality articles or reviews is the crucial to be a focus
for the people to pay a visit the web page, that’s what this web page is providing.
Good day! Do you know if they make any plugins to assist with Search Engine Optimization? I’m trying to get
my blog to rank for some targeted keywords but I’m
not seeing very good results. If you know of any please share.
Kudos!
This website truly has all the information I wanted concerning this subjecct and didn’t know who to ask.
Pretty! Thhis was a really wonderful post. Thank you
for providing this info.
I’ll let Becky, one of the veteran coconut oil users, explain this to you:.
Scalp massage promotes hair growth by reducing stress and tension. Commercial shaving creams usually consist of some sort
of animal-based or hydrogenated vegetable-based
fat, such as stearic acid, chemicals meant to create the right texture
and p – H, fragrances and dyes, and water.
Luxuriously crafted in pure silk, the glossy
black skirt incorporates a smoky flame print licking
up the hem.
I know this website provides quality dependent posts and extra stuff, is there any other site which offers
such data in quality?
As well as i really want at the very least one with pear in it.
Greater made me covet and also search pear fragrances.
Surprising for Religious Dior, he does not consistently hit
the mark with the fragrances however I like this one.
A great task by Dior … I simply think it might have better durability, yet sillage is great.
I absolutely like the odor of a guy which uses this scent.
Thanks for sharing your thoughts about medical negligence
claims. Regards
It’s really a nice and useful piece of information. I’m happy that you just shared this useful info with us.
Please keep us up to date like this. Thanks for sharing.
I found just what I was needed, and it was enttneainirg!
TAMMY IM OLDE FASHIONEDUNDER THE SPREADING BOUGH A LOAF OF BREAD A JUG OF WINE AND A LEG OF MUTTON( SHELLY GOT THE TRANSLATION WRONG) I ADDA NATIONAL MATCH STAR GAUGE SPRINGFIELD!
Thanks for the marvelous posting! I certainly enjoyed reading
it, you will be a great author. I will remember to bookmark your blog and will come back from now on. I want to encourage you to definitely continue your great work, have a nice holiday weekend!